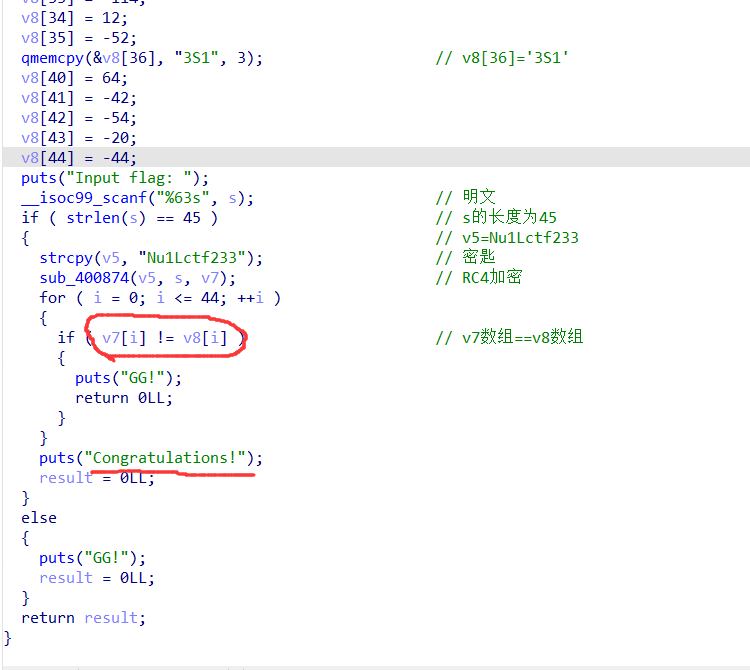
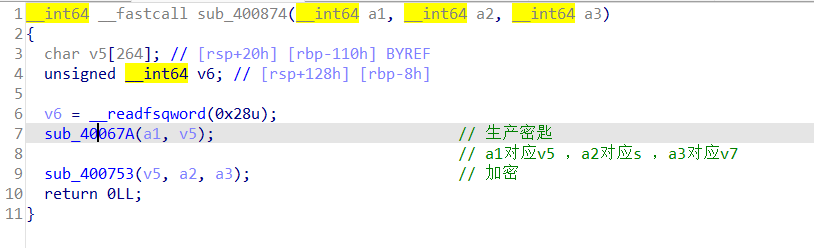
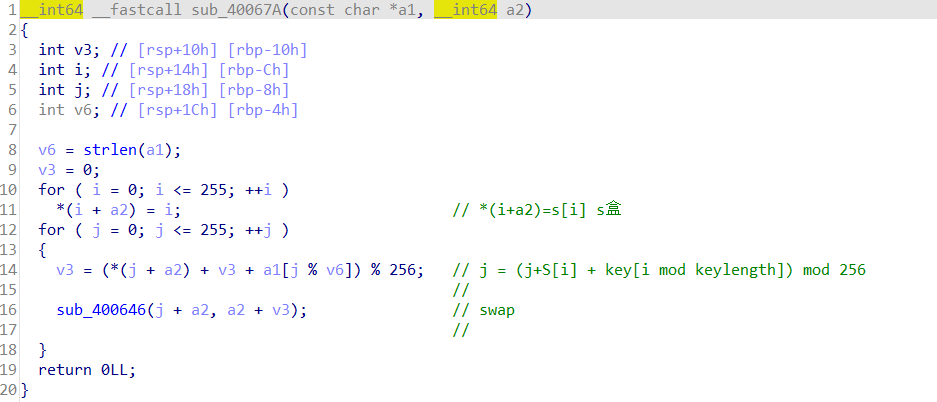
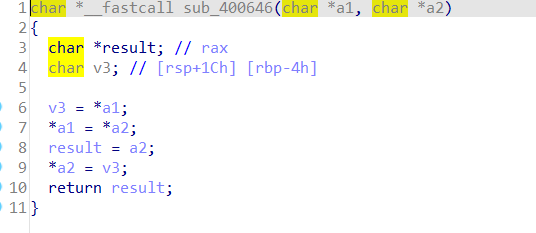
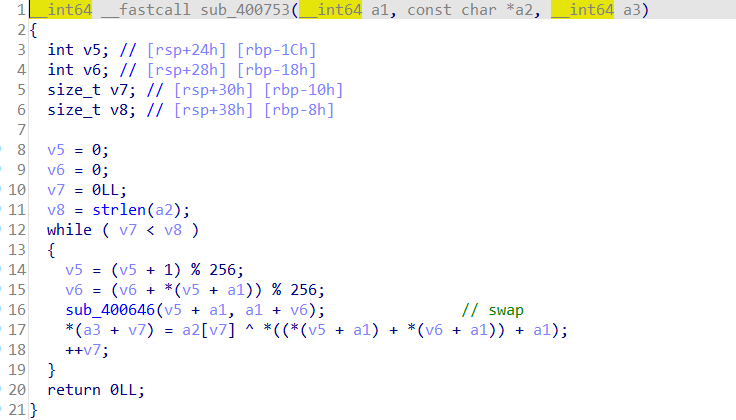
#include<stdio.h>
void rc4_init(unsigned char* s, unsigned char* key, unsigned long Len_k)
{
int i = 0, j = 0;
char k[256] = { 0 };
unsigned char tmp = 0;
for (i = 0; i < 256; i++) {
s[i] = i;
k[i] = key[i % Len_k];
}
for (i = 0; i < 256; i++) {
j = (j + s[i] + k[i]) % 256;
tmp = s[i];
s[i] = s[j];
s[j] = tmp;
}
}
void rc4_crypt(unsigned char* Data, unsigned long Len_D, unsigned char* key, unsigned long Len_k)
{
unsigned char s[256];
rc4_init(s, key, Len_k);
int i = 0, j = 0, t = 0;
unsigned long k = 0;
unsigned char tmp;
for (k = 0; k < Len_D; k++) {
i = (i + 1) % 256;
j = (j + s[i]) % 256;
tmp = s[i];
s[i] = s[j];
s[j] = tmp;
t = (s[i] + s[j]) % 256;
Data[k] = Data[k] ^ s[t];
}
}
int main()
{
unsigned char key[] = "Nu1Lctf233";
unsigned long key_len = sizeof(key) - 1;
unsigned char data[] = {
0xC6, 0x21, 0xCA, 0xBF, 0x51, 0x43, 0x37, 0x31, 0x75, 0xE4,
0x8E, 0xC0, 0x54, 0x6F, 0x8F, 0xEE, 0xF8, 0x5A, 0xA2, 0xC1,
0xEB, 0xA5, 0x34, 0x6D, 0x71, 0x55, 0x08, 0x07, 0xB2, 0xA8,
0x2F, 0xF4, 0x51, 0x8E, 0x0C, 0xCC, 0x33, 0x53, 0x31, 0x00,
0x40, 0xD6, 0xCA, 0xEC, 0xD4 };
rc4_crypt(data, sizeof(data), key, key_len);
for (int i = 0; i < sizeof(data); i++)
{
printf("%c", data[i]);
}
printf("\n");
return 0;
}
|